Introduction
Cameyo empowers organizations of all sizes to simply, securely, and cost-effectively deliver legacy Windows, internal web and internet-facing apps to users from a single pane of glass.
Amazon Web Services (AWS) customers simply install Cameyo on a Windows Server 2016 or above in their account.
The following deployment guide provides step-by-step instructions on how to set up and manage Cameyo, as well as information on the architecture, security, cost, sizing, health monitoring, backup and recovery, maintenance and how to contact Cameyo for support.
Please contact support@cameyo.com if you have any technical questions.
Time required: 1-2 hours
Prerequisites
To get started hosting Cameyo on AWS, you will need the following:
- A Cameyo account.
- If you don't already have a Cameyo account, please go to https://cameyo.com/free-trial to sign up for a free trial. Note: Be sure to use your business email address.
- Credentials to get started will be emailed to you. If you don't receive your credentials, please email sales@cameyo.com.
- An AWS account
- Server instance running Windows Server 2016 or 2019.
- This server will host the applications that the users will access through Cameyo.
- Configuration
- Networking rules allow access to the application server (e.g. via port forwarding), so users are able to access their applications.
- These connections will be over TCP port 80 (HTTP) and/or 443 (HTTPS).
- See here for more information about ports and addresses used by Cameyo.
Skills Needed: No particular skills are needed for the Cameyo installation, but you might need someone with basic AWS administration skills to create the servers and configure the networking on the AWS side.
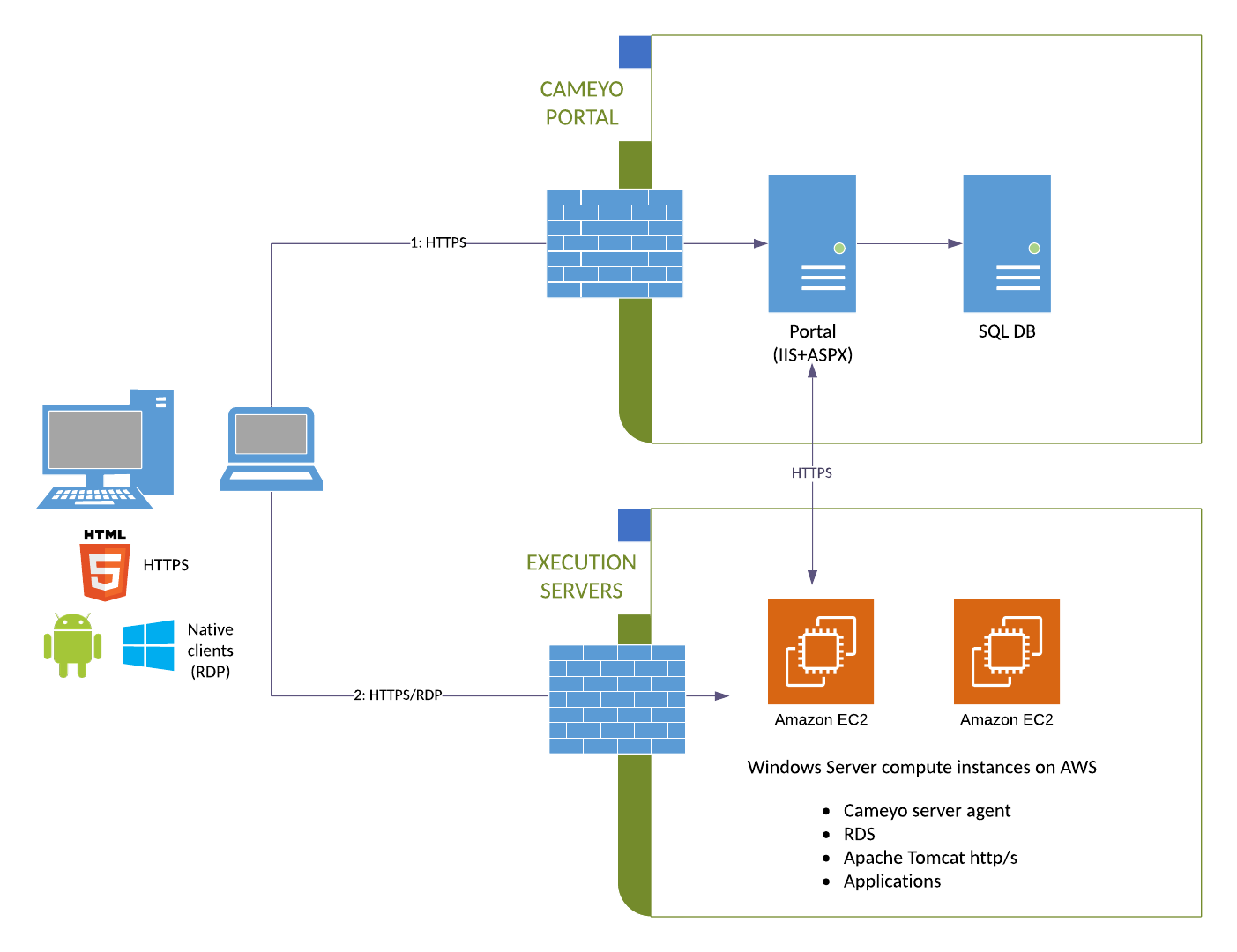
Architecture
Session workflow
- User requests to initiate an application by invoking a "play" action URL from the Portal in the form: https://online.cameyo.com/apps/1234..../play. This can also be invoked through a Cameyo API.
- Portal checks the user's authentication for this application. If authentication is required but missing, the portal authenticates the user either through login credentials or the configured SSO provider. SSO can be any OIDC-compliant provider, including Azure AD, Google, Okta, Ping etc.
- Portal determines the best execution server to serve the request. If there is more than one server, it performs load-balancing based on each server's available resources (CPU + RAM), number of current sessions running on that server, and distance from the user. In cloud environment the portal orchestrates cloud instances as needed, including powering up and/or cloning new servers as needed.
- Portal contacts the best-available execution server and instructs it to prepare to host a session for the request app for that user.
- Execution server performs any necessary preparations, including provisioning the user's Windows profile and synchronizing the user profile's data (registry & files) if SessionSync is enabled. If the client is RDP-based (as opposed to HTML5), Cameyo's RDP Port Shield opens RDP port for the user's IP.
- Execution server responds to the portal with the connection details. The portal translates them to the client:
- HTML5 client: user's browser is forwarded directly to the server's HTTP/S address with a given token. That token is then verified by the execution server against the portal.
- Native Windows / Android rdp clients: connection is made directly through RDP, using one-time credentials generated on-the-fly and transmitted to the client.
- Session runs according to Cameyo's policy settings such as: maximum time / idle time, cloud storage virtualization / synchronization, shell lockdown, toolbar options, file transfer permissions etc.
- Upon session's end, user profile is cleaned up. If Cameyo is configured to "Temporary User Profiles", the entire user profile data is wiped out of the server. If SessionSync is enabled, this is done after synchronizing the user's data back to the central / cloud storage.
Components
Client
Cameyo offers two types of clients: HTML5 and Native
- HTML5: published application is accessible through a simple URL, and the session is rendered within the browser. This is the most universal Cameyo client, and is easily accessible from any device anywhere.
- Native clients (Windows, Android): session is performed directly through the RDP port. In such scenario, the relevant execution server's RDP port is opened on-the-fly for the user's specific IP prior to start a session. This client requires a lightweight component installation upon the first user connection. Native clients have some advantages such as redirection of USB, printing and local drives.
Play Servers (Execution Servers)
Execution servers are offered either from the cloud -- pre-configured and provisioned upon need, or self-hosted. Self-hosted servers are automatically configured by Cameyo during installation, without any required prerequisite other than a supported, up-to-date pristine Windows Server. Cameyo also properly sets the file system security permissions for the components it installs.
Each Cameyo server possesses its own ID (GUID) and private key, generated upon installation. The installation and configuration of the following components is made automatically during the server installation:
- RDS: enables multi-session RDP communication into the server.
- Apache Tomcat: hosts HTTP/S for HTML5 sessions.
- Location: C:\RapPrereqs\Tomcat
- Apache Tomcat 9 service (Tomcat9)
- Logs: C:\RapPrereqs\Tomcat\logs
- Configuration: C:\RapPrereqs\Tomcat\conf
- Cameyo's applet files: C:\RapPrereqs\Tomcat\webapps\ROOT
- HTTPS certificate: managed by Cameyo (cloud) or added manually when needed.
- Preconfigured with AJP connector disabled.
- Apache Guacamole server + client.
- Java Runtime for supporting the Apache components.
Cameyo Backend Components
Cameyo's backend server agent is installed on execution servers in C:\RemoteAppPilot and is composed of several Windows components:
- Cameyo's service (RapStartSvc): runs as a SYSTEM service. In charge of auto-updating Cameyo's server agent components and running RemoteAppPilot.exe.
- RemoteAppPilot.exe: manages the entire Cameyo session workflows including interaction with the portal, session setup, initiation, startup, policy enforcement, user profile lifecycle management, and storage synchronization.
- VirtPH.exe + AppVirtDll*.dll: low-level hooks of Windows applications, for implementing helper functions such as: file open / save dialog replacement, cloud storage virtualization, registry virtualization where needed, app compatibility virtualization.
Portal
Cameyo's portal is typically served from the cloud. In rare cases it is offered for on-premises installation as well. It is composed of:
- IIS 10 or higher with ASP.NET with two sites:
- Portal's app site: online.cameyo.com: serves both as front-end user / admin interaction and as a controller and load-balancer for execution servers and sessions.
- Files server: files.cameyo.com: used for distributing the latest back-end components to execution servers.
- MS SQL 2016 or higher: single, multi-tenant database "cameyoonline". Access to this DB is required only by the IIS instance.
Components Diagram
Self-hosted server (on-premises deployment)
Security
Cameyo's Virtual Application Delivery platform is the simplest and most secure way to deliver business critical applications to users in a hybrid and remote work environment. Cameyo's single architecture and zero trust security model includes:
Limited Attack Surface
Cameyo's single architecture eliminates the need for additional gateways and appliances that can fail and become a security issue on their own (e.g., CVE-2019-19781 - Vulnerability in Citrix Application Delivery Controller, Citrix Gateway, and Citrix SD-WAN WANOP appliance).
Port Shield
Cameyo-developed technology provides built-in security that automatically closes RDP, HTTP and HTTPS ports and opens them to authenticated users only when needed.
Additional information can be found at https://helpcenter.cameyo.com/support/solutions/articles/80000212541-cameyo-port-shield-protecting-your-server-from-cyber-threats.
No VPN
All traffic is encrypted and apps are delivered from a secure HTML5 browser, effectively separating the user's device from the corporate network and eliminating the need for VPNs.
Additional information can be found at https://helpcenter.cameyo.com/support/solutions/articles/80000212529-novpn-optimizing-remote-web-browsing-for-wfh-work-from-home-
Cloud Tunneling
Another Cameyo-developed offering eliminates the need to punch holes in corporate firewalls for inbound network traffic, a major attack vector for hackers.
If you need to set up cloud tunneling, please contact Cameyo Support by sending an email to support@cameyo.com.
Non-persistent Servers
Customer user data is removed from the Cameyo server every time the user logs out, and in the very unlikely event that the secure browser is penetrated, the hacker only has access to the user's session and is wiped from the server when the session ends.
Identity and Access Management and Single Sign On Integration
Cameyo implements the OpenID Connect standard (OIDC) so users can connect through your SSO identity provider, e.g., Okta, Ping, Azure AD, etc. We also integrate with OAuth2 for connections through Google Workspaces (formerly G Suite), Office 365, etc.
Additional information can be found at https://helpcenter.cameyo.com/support/solutions/articles/80000212612-sso-integration.
Windows Terminal Services
Cameyo utilizes Windows Terminal Services and temporary user profiles. This ensures users are unable to access admin privileges, settings, and files.
Data Encryption
Information is encrypted using transparent data encryption. It is protected using Azure Defender for SQL and Azure SQL Auditing, and is only accessible to Cameyo's portal servers (IP white-listing).
Additional information can be found at https://helpcenter.cameyo.com/support/solutions/articles/80000212608-user-information-privacy-and-database-protection.
User Roles
Cameyo's user roles was designed to be simple while fitting to most use-cases. The possible roles are:
- Member: the lowest permissions level for a company account, allowing end-users to play application sessions without any interaction with the portal or configuration.
- Admin: the highest permissions level for a company account, allowing to set up and configure servers, applications, apps, and settings.
Privacy
Cameyo is ISO 27001 certified for information and security management. Our independently audited policies and processes ensures customer data and privacy is highly protected. In addition, Cameyo limits the amount of information stored on a Cameyo server.
Additional information on personal information accessed by Cameyo can found at https://helpcenter.cameyo.com/support/solutions/articles/80000212561-personal-information-accessed-by-cameyo
Additional information on our Privacy Policy can be found at https://cameyo.com/privacy
Costs
List pricing for a Cameyo Self Hosted subscription can be found at https://cameyo.com/pricing-self-hosted/.
Because you are running Cameyo in your own AWS account, you are responsible for infrastructure, cloud usage, RDS CALs, and application licensing.
To inquire about potential discounts, please contact Cameyo Sales at sales@cameyo.com.
Sizing/Capacity Planning
Hardware capacity depends on the application that needs to run on the server. It can start from 1 CPU per 12 concurrent users and 2 GB RAM per user for lightweight apps, all the way up to multiple CPUs per session. You can estimate the required capacity for your app by connecting to a server as an admin while several app sessions are being used on it, and looking at the Task Manager's "Users" tab.
Cameyo Analytics is a feature that monitors usage and offers recommendations on server resources to maximize the efficiency of your environment. Access Cameyo Analytics in the Cameyo Admin Console.
Deployment
Once you have a server ready on AWS, please follow our guide on setting up a self-hosted Cameyo server.
After your initial server has been created, get all your applications installed, configured, published, and tested. If anything does not work during your testing, you can use our Knowledge Base for assistance, or you can contact Cameyo support for more advanced troubleshooting.
Once everything is working the way you want it, the next step is to clone that server and create a server cluster, based on the capacity planning you did earlier.
Health Check
Cameyo employs a layered approach to ensure the health of the service.
Health Monitoring
Cameyo runs an automated quality of service health monitoring bot named HealthMon. This bot regularly checks Cameyo's servers, providing indication in case of problem. The test bot's results are indicated in green or red on the server's list:

For more information on Cameyo HealthMon, go to https://helpcenter.cameyo.com/support/solutions/articles/80000212565-automated-server-health-monitoring
Backup and Recovery
In a Cameyo self-hosted environment, you are responsible for managing backups of your servers and recovering in the event of a failure. Because of this, we strongly recommend setting up automated server snapshots that can be reverted to if necessary.
For example, Cameyo fully-hosted environments are snapshotted monthly, weekly, daily, and every 4 hours. We recommend a similar schedule for your self-hosted servers, or choose another schedule that works best for your organization.
Additionally, you may choose to take advantage of AWS's high-availability options, set up a server cluster, or both.
Please work with your AWS contact to determine the backup and disaster recovery options that are the best fit for your organization. The following links to AWS documentation should be a good place to get started:
Cameyo Analytics
Cameyo Analytics is the first Artificial Intelligence driven optimization and reporting solution for virtual application delivery environments. Cameyo Analytics gives you the real-time data needed to proactively identify, troubleshoot, and remediate problems before they become issues that impact your employees’ experience and productivity. To access the reports and recommendations, select Analytics in the Cameyo Admin Console.

Routine Maintenance
In a Cameyo self-hosted environment, you are responsible for keeping your server and applications patched and updated.
The Cameyo virtual application delivery platform will automatically update, so no customer maintenance is needed for it. These automatic updates include new features and capabilities, security updates, platform optimization, and bug fixes. All critical security vulnerabilities will be immediately patched as soon as they are identified and a fix can be developed, while all other updates will go through our standard testing and change management processes before release.
You are also responsible for managing and maintaining your server and RDS client licenses as necessary. See this article for assistance installing RDS CALs on your server.
Cameyo recommends you regularly monitor the usage on your servers and work to resolve issues and optimize resources. This is made much easier using Cameyo Analytics, which is available from the Cameyo admin console.
If you are using Cameyo's API to programmatically manage your account, we strongly recommend regular rotation of the API client secret. You can do this from the Admin > Company Settings page, in the Advanced section, by clicking the "Change key" arrow button. We recommend that you rotate your keys monthly.

Emergency Maintenance
In the rare event that an application stops working please contact Cameyo Support immediately by emailing support@cameyo.com. See the Support section below for details on how tickets are handled and corresponding SLAs.
The most common problems running applications on Cameyo are network-related. Issues may include firewalls blocking access, web filters blocking access, port forwarding not working correctly, proxy servers not being configured correctly, unreliable Internet connectivity, and so on.
The second most common category of application issues are related to the applications themselves. Because Cameyo supports a wide variety of applications, the root causes for these issues are also varied. Some examples of causes include: incorrect application configuration (e.g. pointing to incorrect folders, licensing problems, etc.), insufficient server resources (such as when many users try to get on a server at the same time, overwhelming it), and unstable applications crashing.
In the event that the Cameyo application delivery platform stops working, and it has been verified that the root cause is not related to the application itself, or with a networking-related issue, then it may be necessary to redeploy the Cameyo software on the server. This can be done by pressing the Redeploy button on the server details page of the server hosting the application, or it can be done manually by downloading and running the installer file.
Support
Cameyo's global support is completely free. To contact support, send an email to support@cameyo.com or submit a support ticket here. If you are in the admin console, select Support from the drop down menu at the top right corner of the page. The issue will be logged and ticketed, which allows you to track the ticket through resolution.
Response Time Service Level Agreement
All tickets are reviewed and assigned an SLA level. Response times per level are listed below.
ISO 27001 Certified
Cameyo is ISO 27001 certified for Information Security Management. Our independently audited policies ensure the greatest protection from threats. In addition, we have ISO 27001 certified processes in place for disaster recovery that include recovery time objectives and recovery point objectives. As part of the certification, Cameyo reviews all policies, processes and procedures to remain in compliance. For specific information on our ISO 27001 certified policies, please contact compliance@came





